Much like symmetric-key ciphers are vulnerable to brute force attacks, every cryptographic hash function is inherently vulnerable to collisions using a birthday attack. Due to the birthday problem, these attacks are much faster than a brute force would be. A hash of n bits can be broken in 2 n/2 time (evaluations of the hash function). How to brute force a password? The brute force strategy is to try any possibilities, one by one, until finding the good password For a MD5 hash if the database doesn't find a result, you can use other tools like HashCat or John the Ripper to do this. In the following paragraph, I'll explain you how the brute force is working exactly, which.
Skip to end of metadataGo to start of metadataThis receipe shows how to brute-force open a MacOSX disk image with encryption set if you cannot remember the password any more. Which hard drive for mac.
The approach also works with sparseimage files using AES 128 or 256 bit encryption, as used by MaxOS Sierra 10.12.
Prerequisite is that you do have an idea about what the password may look like, if you can guess most of it's text elements, but something was added or you cannot remember the exact password any more.
Brute Force For Hash Machine
A situation like this:
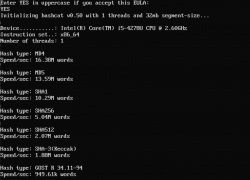
In this case, you can use John The Ripper to brute-force the disk images hash value via a wordlist and rules.
First you need to install 'John the Ripper' (JtR). Best suited is the precompiled MacOS version.
Linux versions available with apt for Debian lack the latest patches necessary for Sparseimage files.
There is a tool 'dmg2john' included in the MacOS distribution, which also runs for Sparseimage files.
The image passwords AES hash is now laid down for JtR in the Secrets.hash file as text:
Assemble a suggestion list for your cracking attempt as a text file. The words that may be part of the password - or any words used by the image owner that could be assembled - can just be written down line after line.
Brute Force For Hash Mac And Cheese
Just run JtR. No additional configuration needed.
In this case, obviously, 'welcome1' has been the password. You can mount the image file now.
Brute Force For Hash Macaroni
You can of course also use a real brute force approach like: 'run/john Secrets.hash' without your own wordlist and just permutate through the character base, but given sufficient password complexity that might be a lengthy approach, fortunately.
Brute Force For Hash Machine Learning
Brute Force For Hash Mac Dre
See also: Password Cracking AES-256 DMGs and Epic Self-Pwnage
